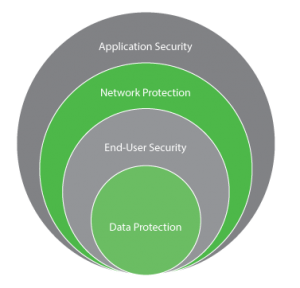
Cyber Security: The Onion Approach

Cyber Attack Threats
Common security threats include viruses, worms, spyware, and ransomware, but the methods of cyber-attack are constantly evolving. This creates a need for constant monitoring and multiple layers of defense. A multi-layered approach is set in place to reduce opportunities and access points for attackers. The idea is as simple as it sounds; instead of having only one layer of defense, you employ several layers, making it more difficult for cyber criminals to launch a successful attack.
Protection
Most businesses employ antivirus software. It was originally created to protect computers from malware by relying on comparisons to file signatures. Antimalware is another important component to consider for your protection. Antimalware seeks out anomalies and indicators of bad behavior improving endpoint protections. While these are still valuable components of Cyber Security, they should not be the only technology used to protect your network and devices.
To combat evolving threats, create an entire ecosystem of layered security – data protection, end-user security, network protection and application security.
The Layered Approach
Data Security
When talking with “tech guys” don’t be surprised to hear “back-up your data” MANY times. Data is arguably the most valuable asset in your company network. Operating systems and applications can be restored but that isn’t always the case when restoring original data.
We recommend backing up company, financial, and client data on a regular basis. Regular means daily, sometimes hourly. Backing up your data involves encrypting and copying files over to a secure, off-site system. Backups are retained in a schedule. This means you can restore data to a given point in history – such as before a virus was installed. Should you need to restore them, your company can be back in operation in a matter of hours instead of days or weeks.
Email security
Email security is a priority for all businesses for many reasons. It’s the primary entry point for many viral and malware attacks. Research has shown that 9/10 viruses that infect computers stems from an email attachment. This makes it a vital area to protect.
Ensure you are using a good spam filter and scanning email attachments. For added protection, email encryption can protect privacy for individual emails, keeping data and messages safe between sender and recipient. Always make sure email and device passwords are strong and kept private.
One of the best ways to ensure email security is educating your staff and establishing policies for best practices. These may include only opening emails from reliable sources and only clicking links in emails from sources you trust.
Endpoint protection
Endpoint protection refers to protecting the networks that are remotely bridged to your devices such as the connection of your laptop, tablet, and mobile phone. The connection of these devices creates paths for security threats.
End user training is very important for business security. End users are anyone who utilize your network or have devices connected to your network. Arming your team with knowledge is key in preventing breaches. JFG conducts trainings for client teams in security awareness and best practices.